Discover & map your full attack surface.
Our automated solutions identify and catalog known and unknown domains, hostnames, and IP addresses exposed to the internet.
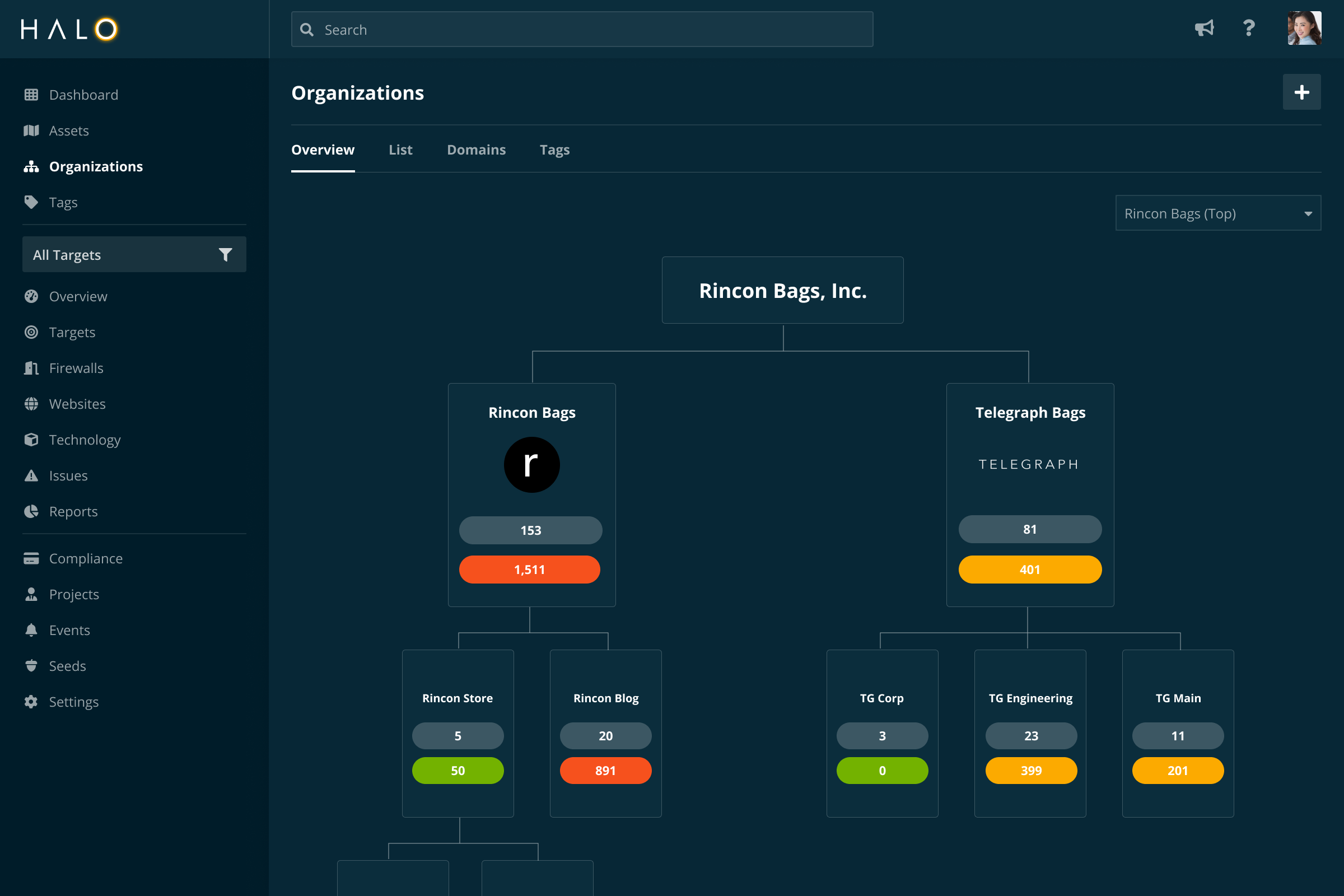
Halo Security gives you immediate visibility into the risk posture of subsidiaries and organizational units.
Subsidiaries and acquisitions introduce new risks, and take time to fully integrate. Halo Security takes the attacker’s perspective to give you deep visibility into the external risk posture of subsidiaries and acquisitions with no installation or configuration required.
Watch Video Try It FreeOur automated solutions identify and catalog known and unknown domains, hostnames, and IP addresses exposed to the internet.

The rich data we collect brings you the context you need to understand what the asset is, what’s running on it, and who’s responsible for it.
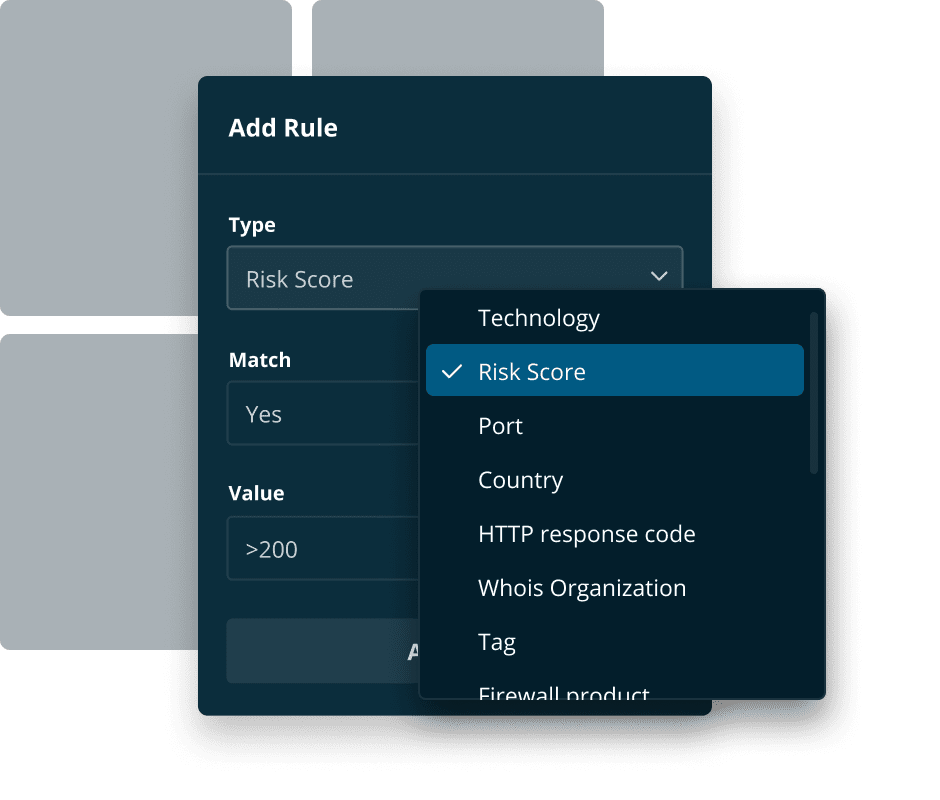
Track and rate the security posture of subsidiaries.
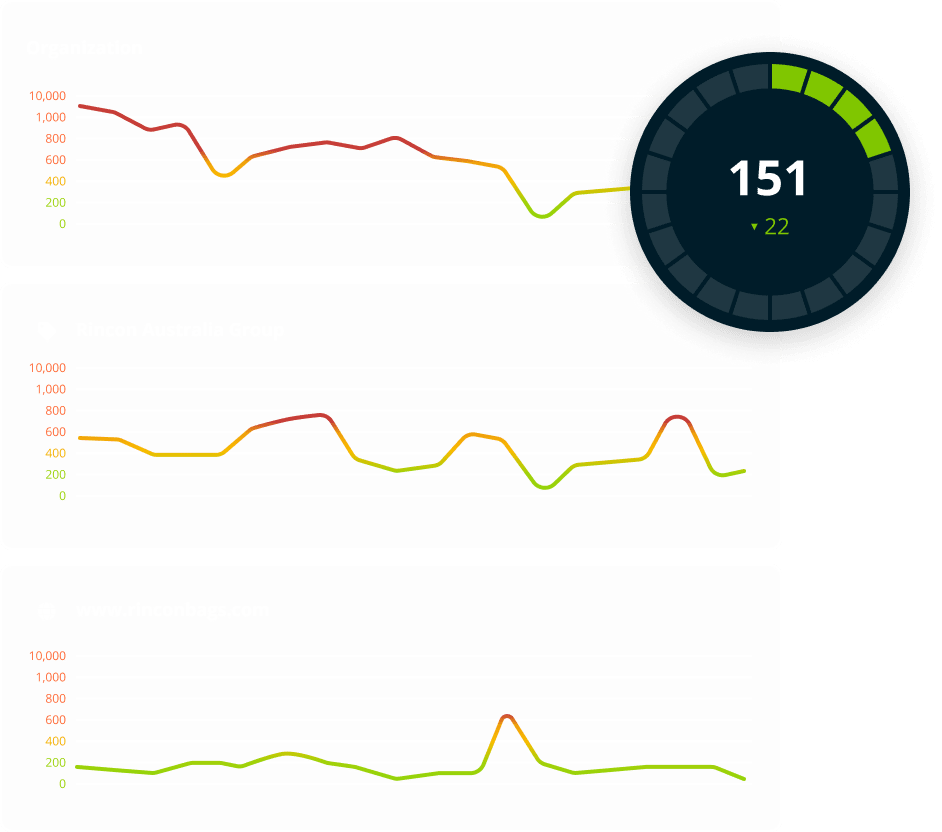
Let us show you a complete picture of your external attack surface. Our agentless, non-invasive technology allows us to bring you actionable insights from your very first demo.
Schedule a Demo



