Discover your assets
Know what's exposed.
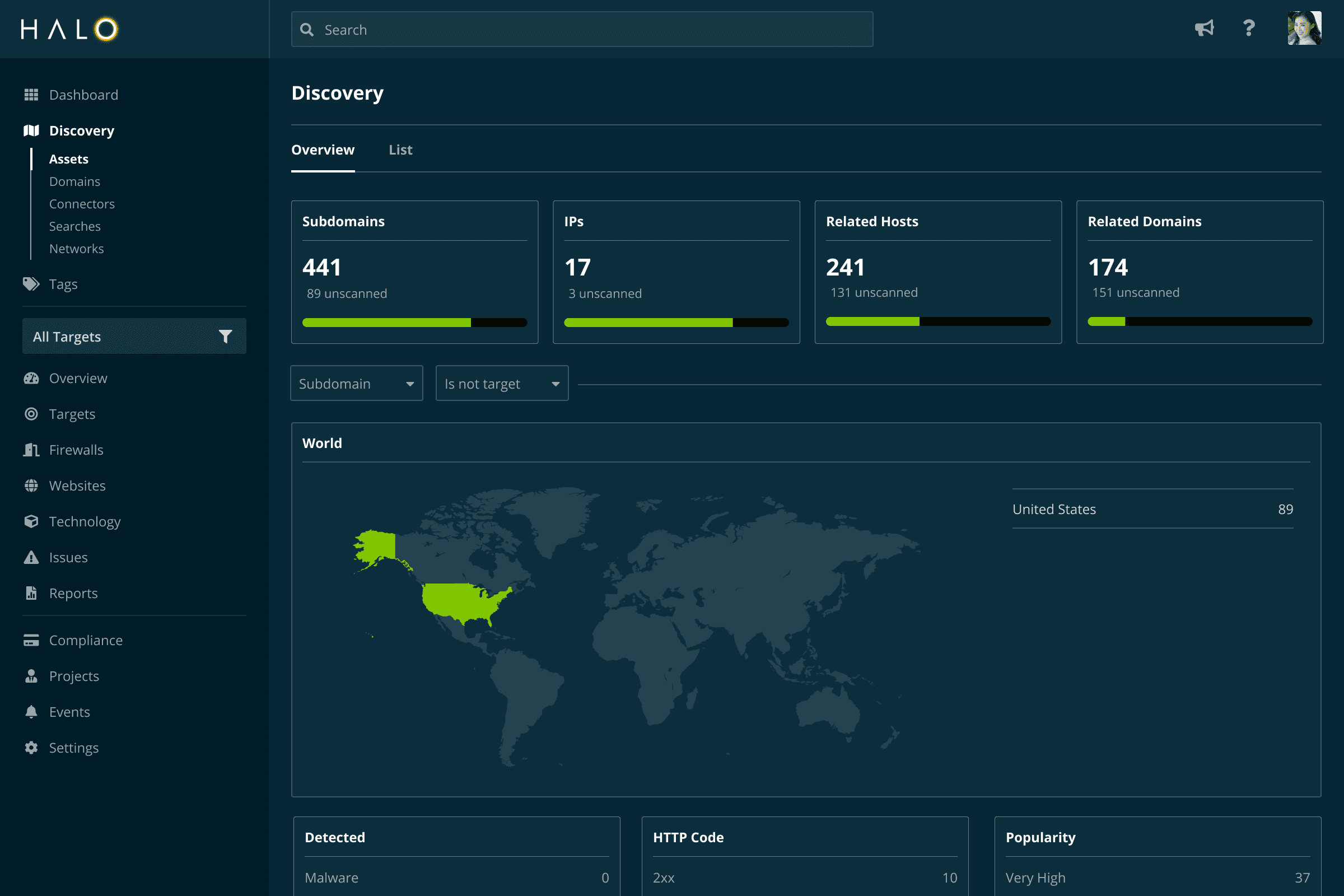
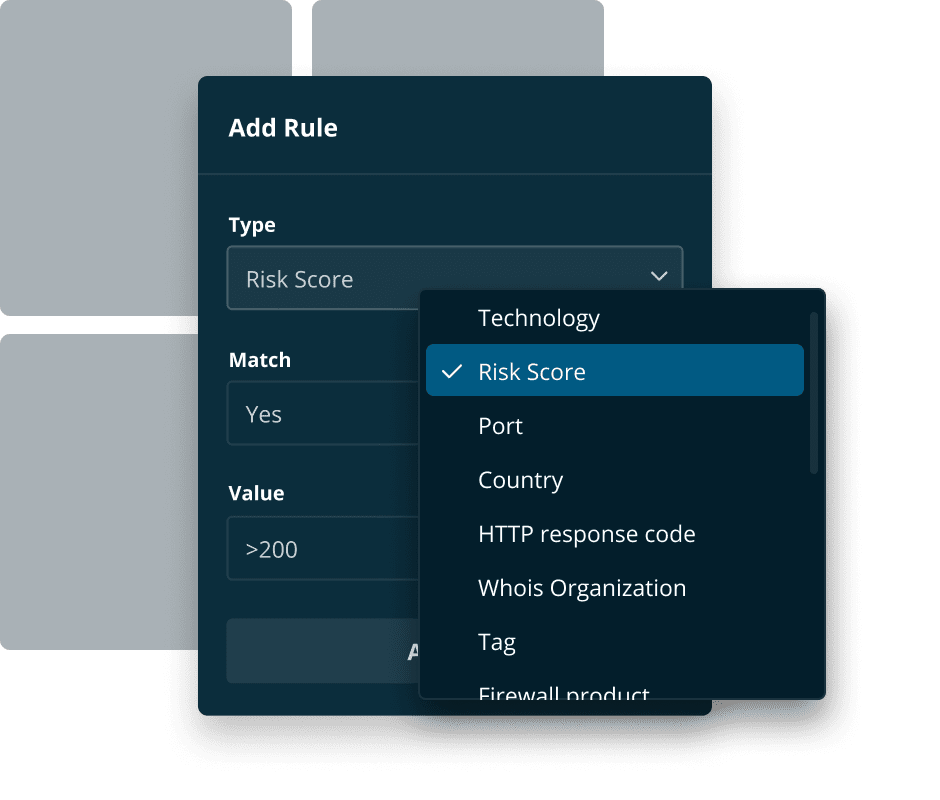
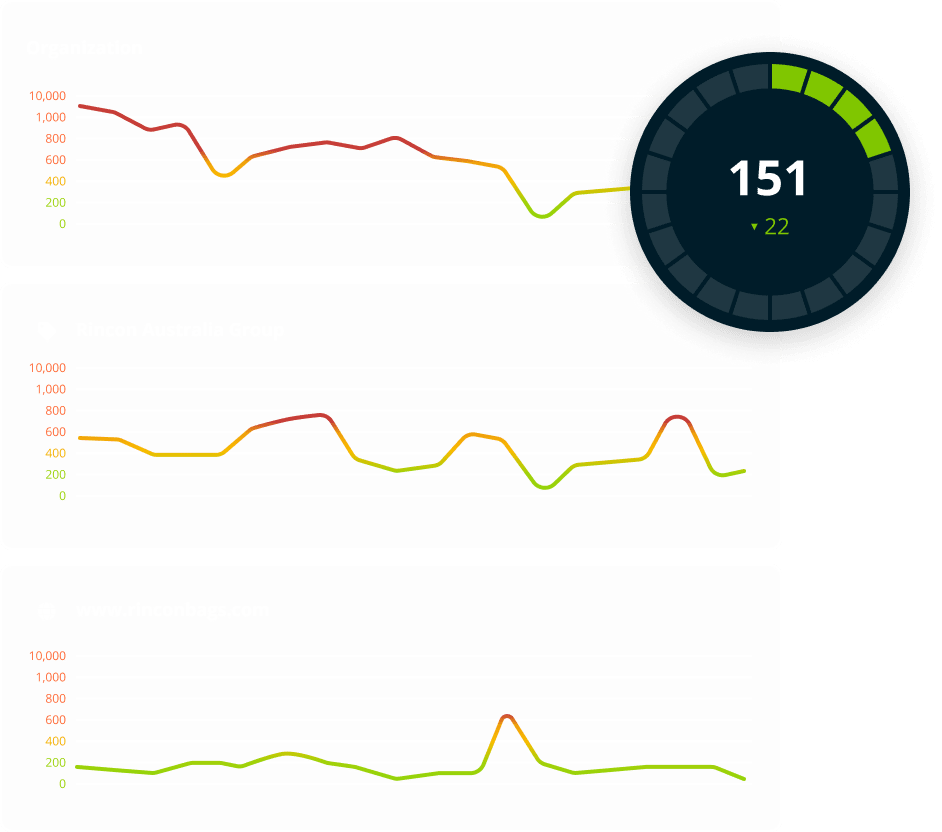
Traditional vulnerability scanning solutions rely on you entering the IP addresses you want to scan. But what about the assets you’re not aware of?
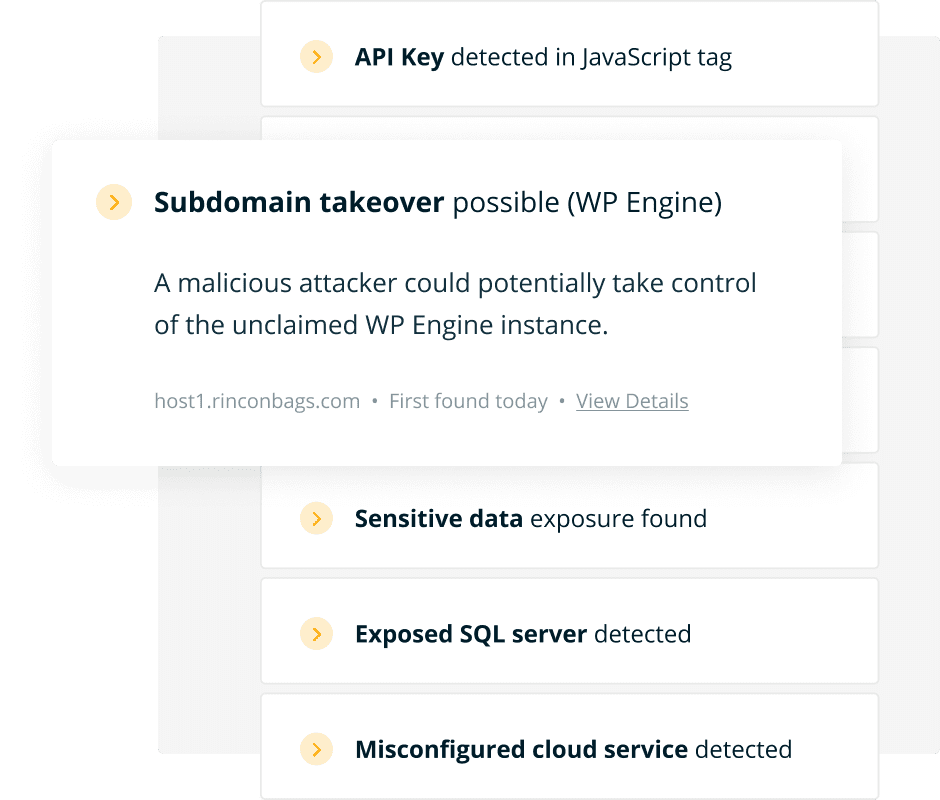
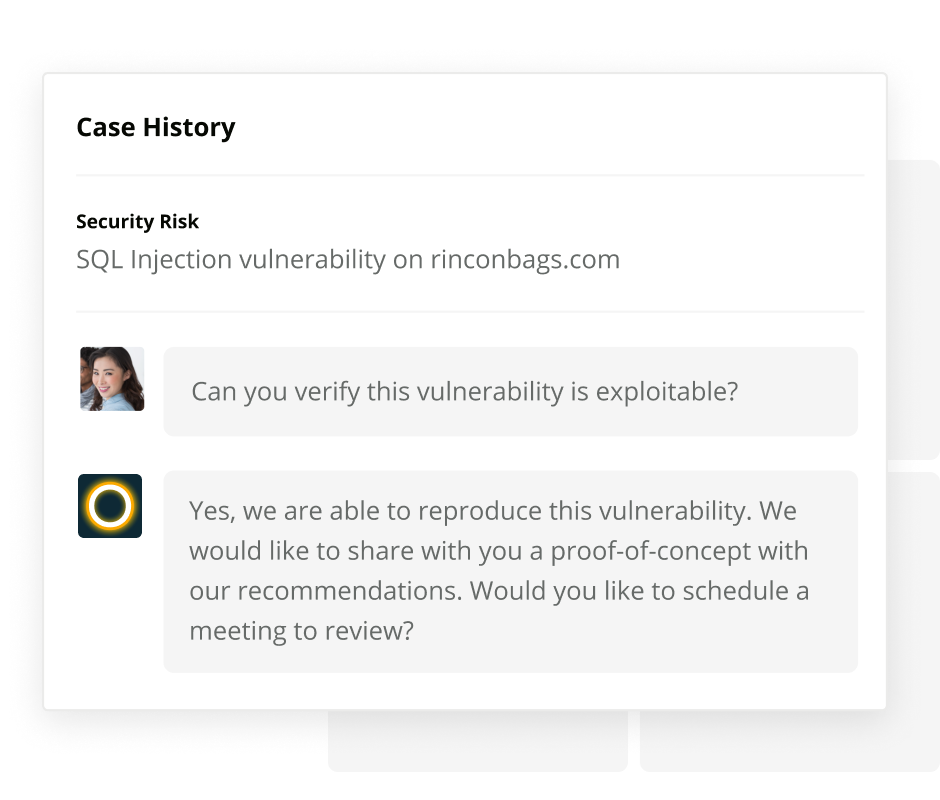
Like an attacker or experienced penetration tester, Halo Security starts by identifying the assets you own to ensure you have full visibility into your external vulnerabilities.