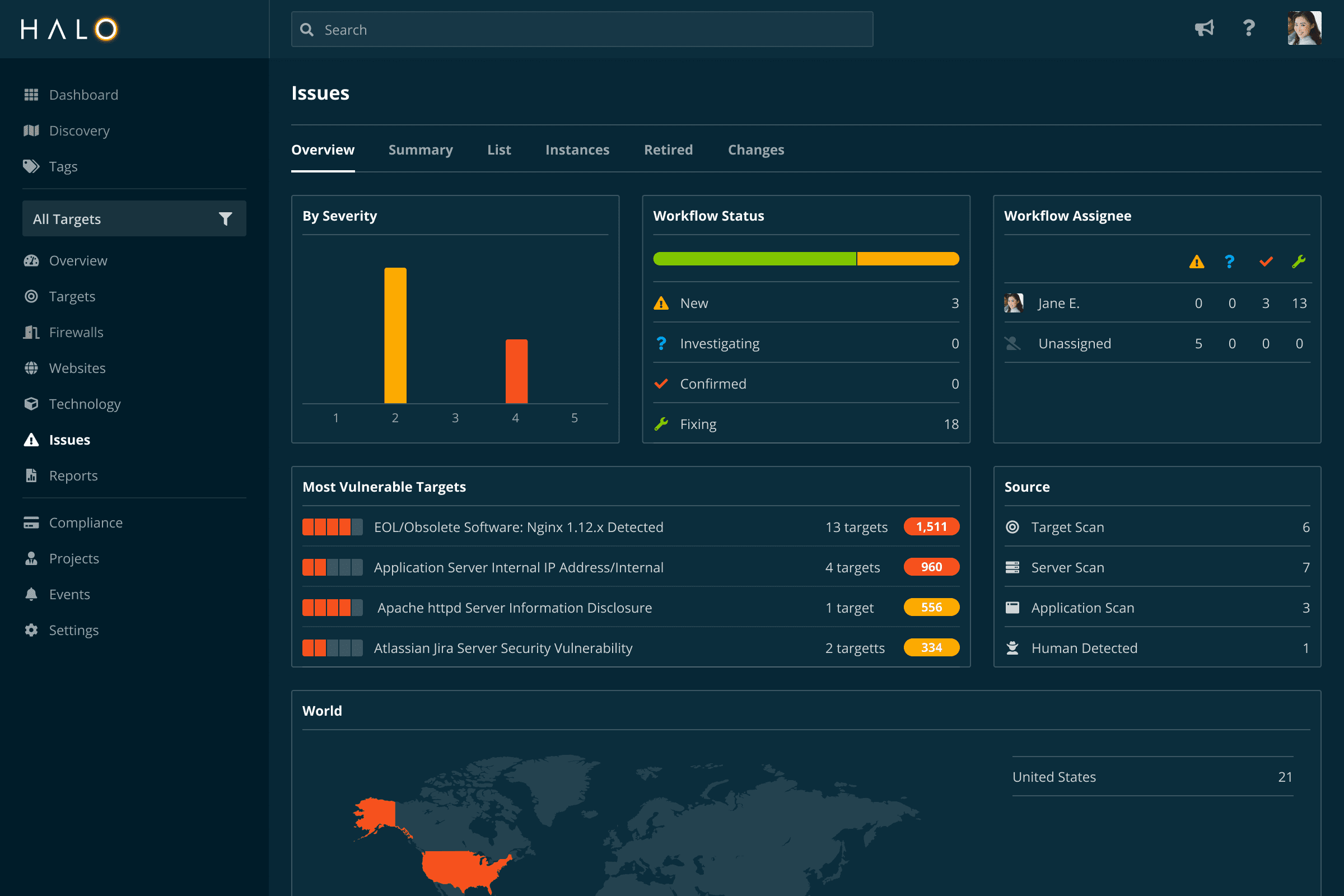
Identify coding flaws and security weaknesses on your websites and applications that could be used to exploit your business.

Detecting vulnerabilities in your custom web applications is critical as they can pose a significant risk to your business. By proactively testing the security of your web applications, you can stay ahead of attackers and protect your valuable assets.
Application Scanning uses the Dynamic Application Security Testing (DAST) approach to help you discover custom web application vulnerabilities such as SQL Injection, Cross-Site Scripting, Cross-Site Request Forgery, and OWASP Top 10 Security Risks, and SANS CWE TOP 25 Most Dangerous Software Errors.
Our application scanning tool goes beyond the surface to automatically detect and prioritize vulnerabilities listed in the OWASP Top 10. By leveraging industry-standard methodologies and exhaustive scanning techniques, our platform ensures that your applications are thoroughly scrutinized for prevalent security flaws. From Injection vulnerabilities to Broken Authentication and Session Management, we provide actionable insights to help you fortify your defenses against the most critical threats identified by OWASP.
SQL Injection remains one of the most prevalent and dangerous vulnerabilities threatening web applications today. Our application scanning feature is designed to automatically identify and flag SQL Injection vulnerabilities, empowering you to take swift action to mitigate this serious risk. By systematically analyzing your applications for SQL Injection vulnerabilities, our platform ensures that your sensitive data remains secure and protected from exploitation by malicious actors.
Cross-site Scripting (XSS) vulnerabilities pose a significant threat to web applications, potentially leading to unauthorized access, data theft, and other malicious activities. Our application scanning tool is equipped to automatically detect and highlight XSS vulnerabilities, enabling you to promptly address these critical issues. By uncovering XSS vulnerabilities in your applications, our platform helps you bolster your security measures and safeguard your users' data from exploitation.
Application Scanning runs on your schedule, so you can quickly identify new vulnerabilities as they appear. With our event tracking system, you can easily audit when past changes occurred or configure real-time alerts via email, Slack, or your favorite ticketing tools.
We look at your organization from the outside. There’s nothing to install and nothing to configure.
Our intuitive dashboard is easy to use, but gives you the flexibility you need to view and filter your data the way it makes sense to you.
Our experts are here to help with every question you have, and provide the advice you need to thrive.
Start your free trial or schedule a complimentary attack surface assessment today.
Get a DemoOr see plans & pricing »




