Tell us what you know. Let us find the rest.
Our recursive discovery process identifies known and unknown internet-facing assets, and suggests new seeds to further discover your full attack surface.
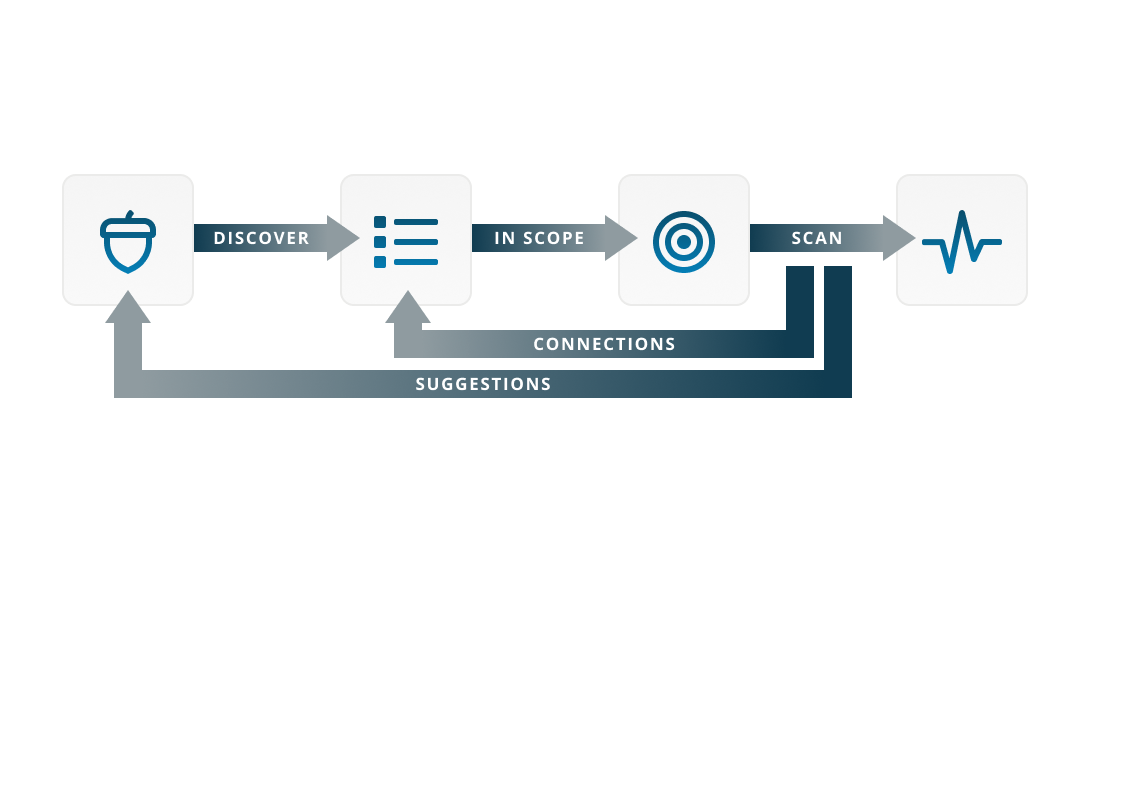
Halo Security automatically discovers internet-facing assets that belong to your organization and and allows you to easily and automatically assign them to the responsible teams.
Traditional scanning solutions were designed for traditional networks. Halo Security takes the attacker’s perspective to help you discover external assets across clouds, third-party providers, and organizational silos.
Watch Video Try It FreeOur recursive discovery process identifies known and unknown internet-facing assets, and suggests new seeds to further discover your full attack surface.

The rich data we collect brings you the context you need to understand what the asset is, what’s running on it, and who’s responsible for it.
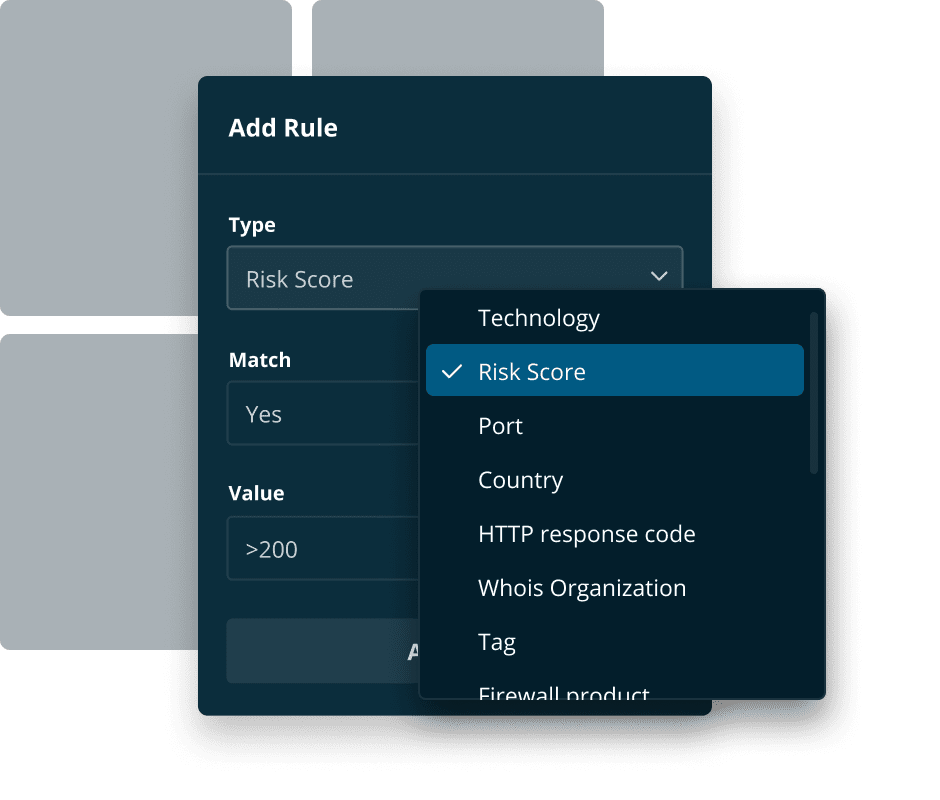
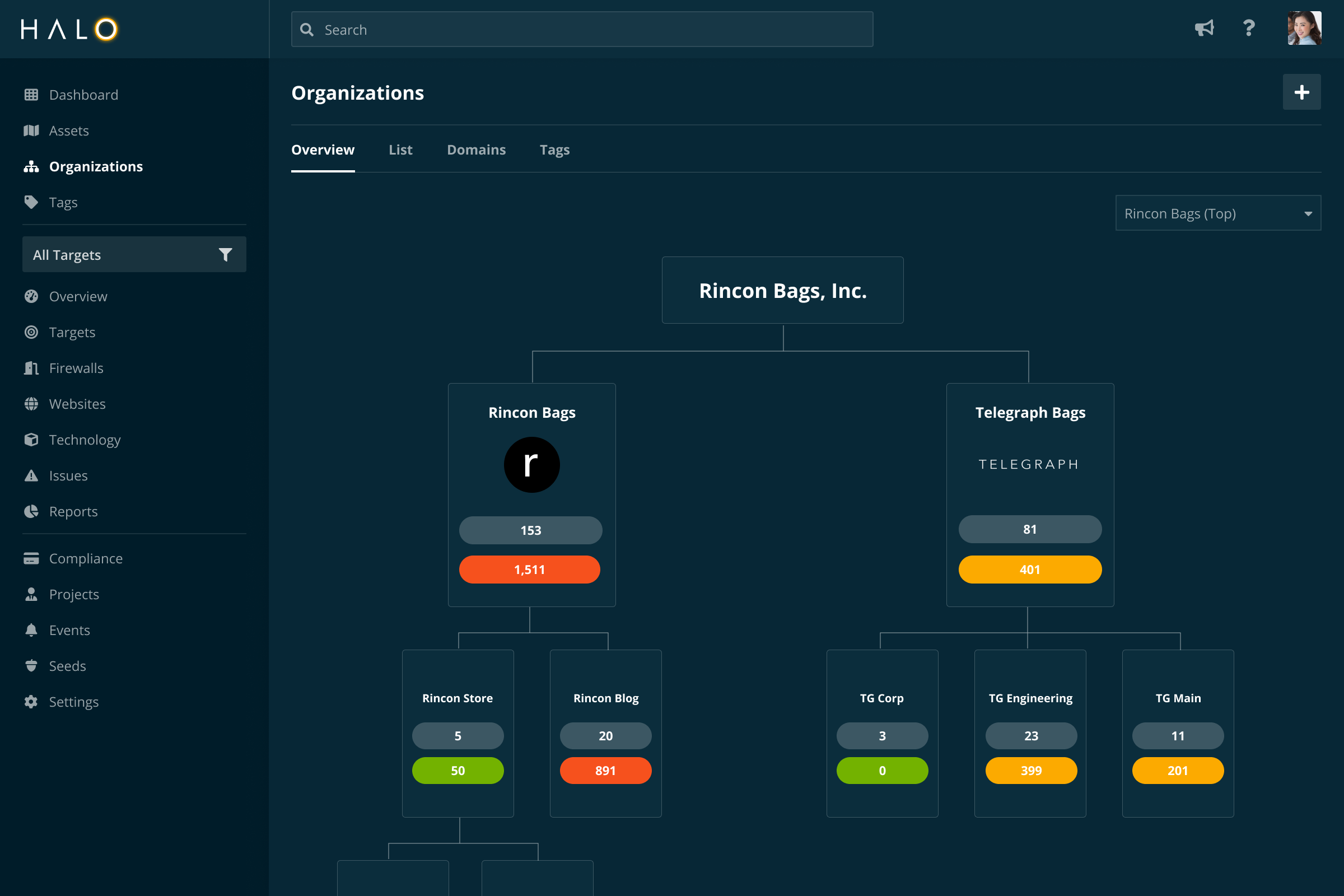
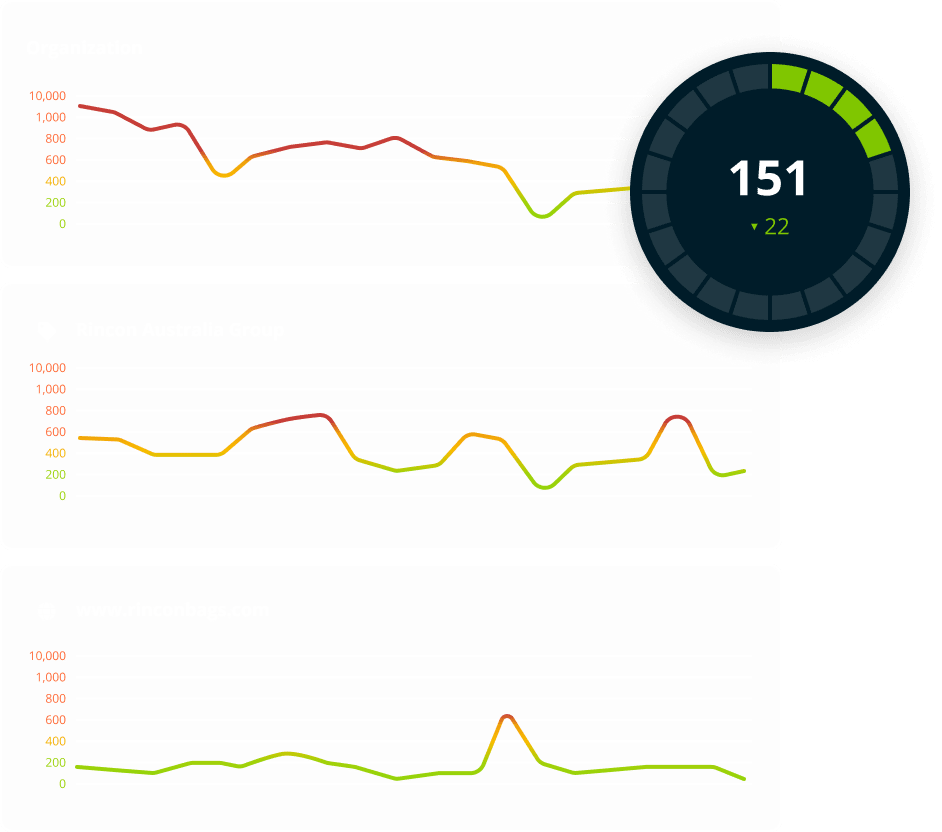
Measure and report on your external risk posture, while prioritizing the issues that matter most.
We offer agentless scanning and single-pane-of-glass visibility out of the box. But we also make it simple to move your data where it makes sense for you.
Let us show you a complete picture of your external attack surface. Our agentless, non-invasive technology allows us to bring you actionable insights from your very first demo.
Schedule a Demo



