Quickly and easily discover, monitor, and secure your internet-facing assets. Get unmatched visibility, pinpoint risks, and act with confidence—before attackers do.
7-Day Free TrialTraditional vulnerability and risk management solutions were designed for traditional networks. Halo Security takes the attacker’s perspective to help you identify, assess, and monitor the risks across clouds, third-party providers, and organizational silos.





You can't protect assets you don’t know about. Our automated solutions identify and catalog known and unknown domains, hostnames, and IP addresses exposed to the internet.
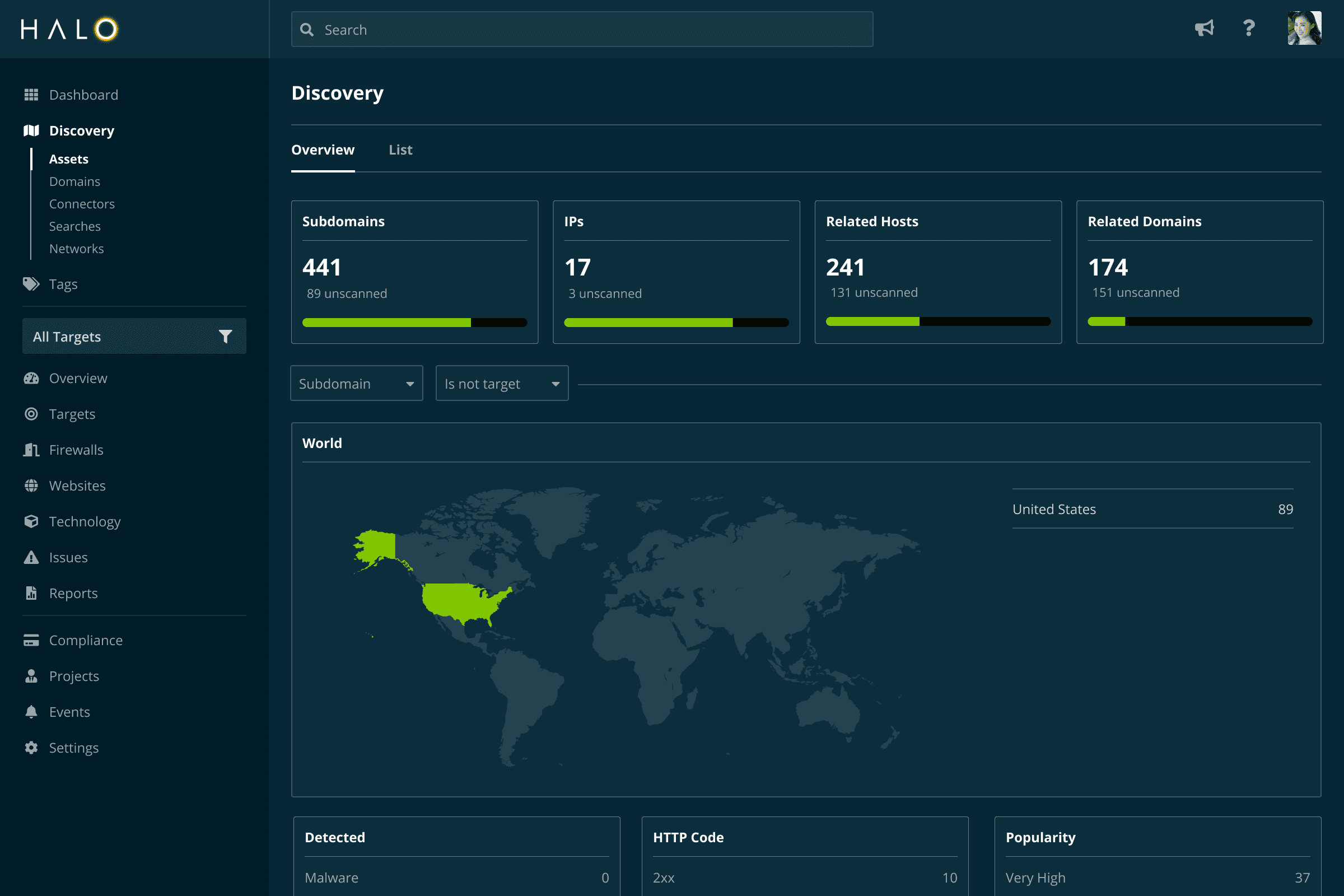
The rich data we collect brings you the context you need to understand what the asset is, what’s running on it, and who’s responsible for it.
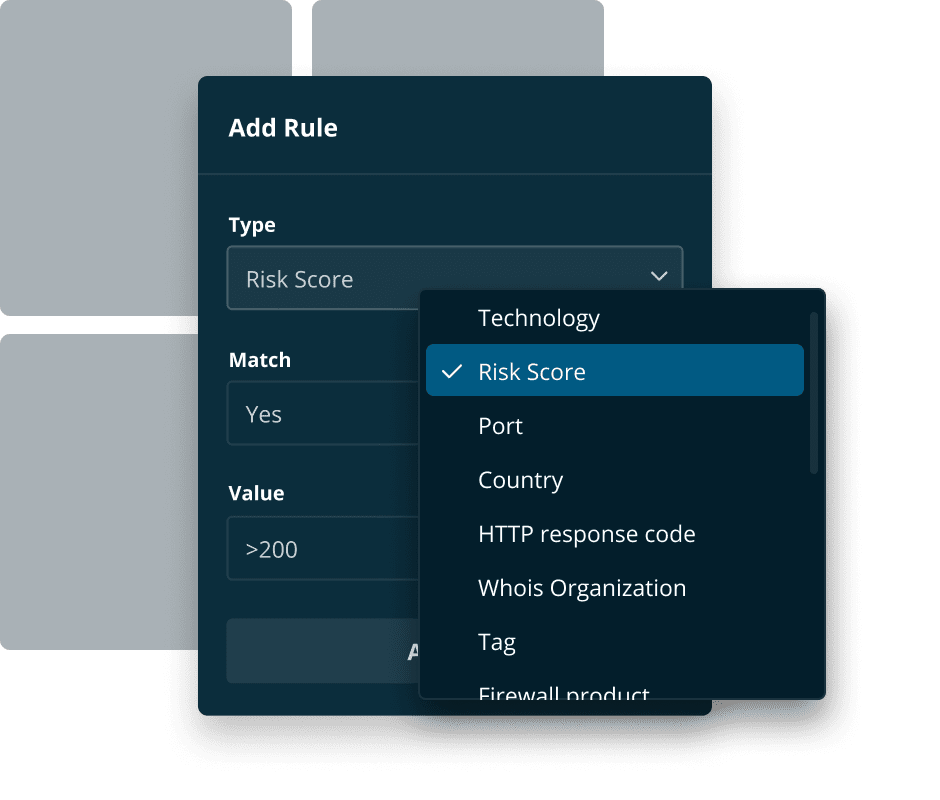
Our agentless vulnerability detection is tuned for internet-facing assets and goes beyond simply detecting known vulnerabilities (CVEs). And yes, we detect those too.
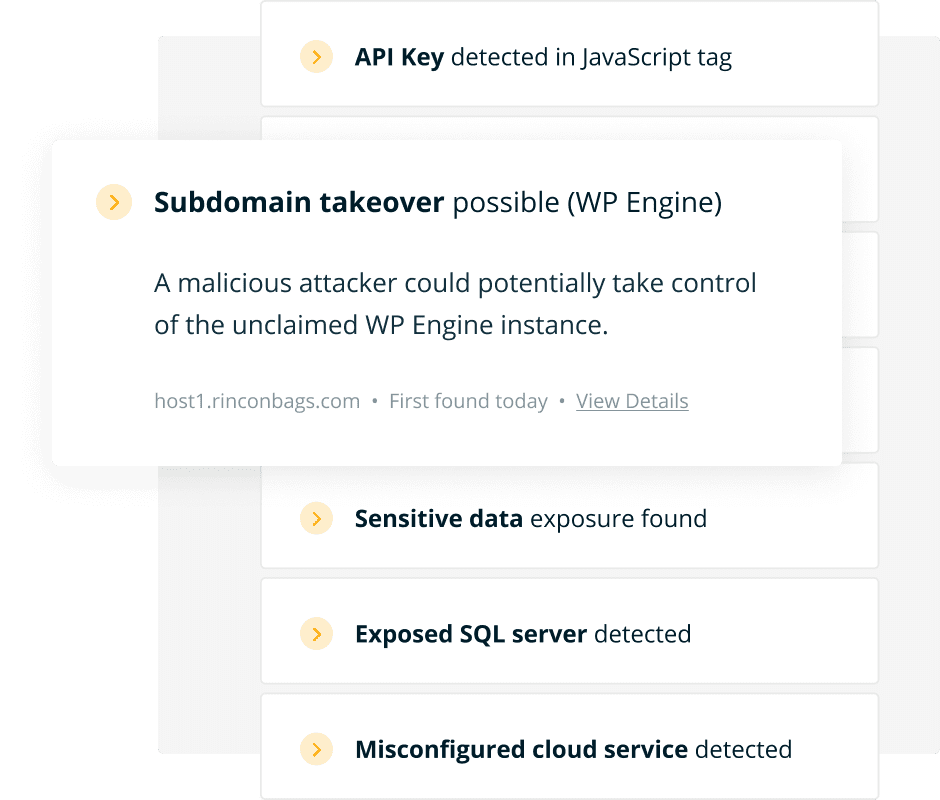
Measure and report on your external risk posture, while prioritizing the issues that matter most.
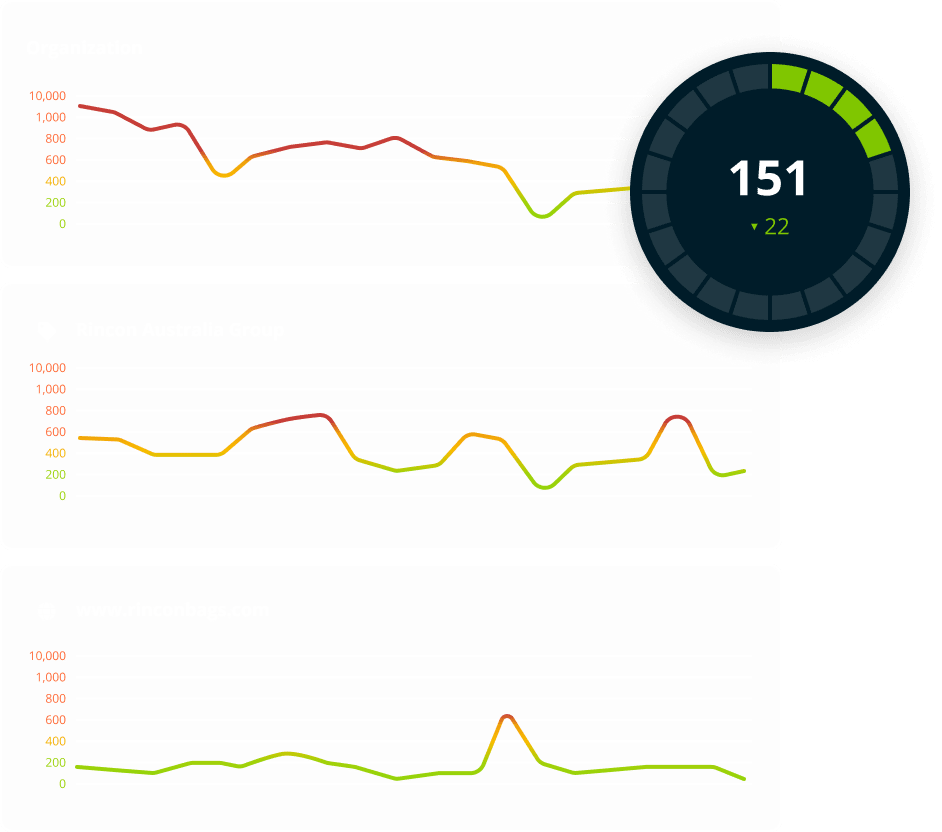
When the next Log4j strikes, you don’t want to be caught running manual exercises to find out if you’re using that software. The Halo Security platform makes it easy to find the most critical insights about your attack surface in seconds.
We offer agentless scanning and single-pane-of-glass visibility out of the box. But we also make it simple to move your data where it makes sense for you.
Continuous vulnerability detection and prioritization helps you efficiently eliminate risks.
With automatic categorization and zero installation, it's easy to measure and evaluate subsidiaries.
Achieve your compliance goals faster with Halo Security, a PCI DSS Approved Scanning Vendor (ASV).
We offer comprehensive vulnerability scanning fine-tuned for internet-facing assets.
Easy-to-use dynamic application security testing (DAST) helps you evaluate custom web applications.
Our integrated manual penetration testing services help discover issues automation can’t find.
We’re a private, woman-owned business founded in 2013. We’re led by ethical hackers and software engineers. Our roots in external risk management stem back to 2001, when our CTO developed one of the first commercial vulnerability scanners.
100% funded by our users.

Per Month
Our free trial gives you 7 days of full access to Halo Security’s external exposure management platform. You can discover and scan up to 100 internet-facing assets, identifying vulnerabilities, misconfigurations, and other security risks across your entire attack surface. This trial is designed to give you complete visibility into your external exposure so you can experience the power of our discovery, monitoring, and assessment solutions.
Getting started is simple — all you need is a domain name. Halo Security will automatically map your entire attack surface, discovering every internet-facing asset and assessing them for vulnerabilities and misconfigurations. You’ll see your first exposure assessment results in minutes, giving you instant visibility into your organization’s external risk profile so you can take action before attackers do.
External Exposure Management is the process of continuously discovering, monitoring, and securing all internet-facing assets that make up your attack surface. It provides security teams with complete visibility into their external footprint, identifies vulnerabilities and misconfigurations, and enables proactive remediation before threats can be exploited. Halo Security’s platform automates exposure management to help organizations stay ahead of evolving cyber risks.
An Exposure Assessment is an in-depth analysis of your organization’s external attack surface to identify vulnerabilities, security misconfigurations, and other exposures that could be exploited by attackers. By understanding your external risk posture, you can prioritize remediation, strengthen your defenses, and reduce your overall attack surface. Halo Security performs exposure assessments as part of its external exposure management platform, giving you actionable intelligence to protect your organization from cyber threats.
Let us show you a complete picture of your external attack surface. Our agentless, non-invasive technology allows us to bring you actionable insights before you ever see a contract.
Schedule a demo